](https://s.yimg.jp/images/tecblog/2016-1H/os_n_k8s/kubernetes.png)
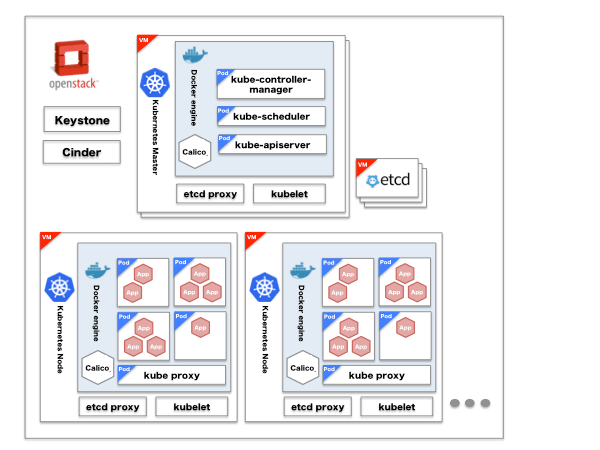
|Product |Description |
|OpenStack Keystone|Kubernetes Authentication and Authorization |
|OpenStack Cinder |External volume used from Pod (grouping of multiple containers) |
|kube-apiserver |Configure and validate objects like Pod or Services (definition of access to services in container) through REST API|
|kube-scheduler |Allocate Pods to each node |
|kube-controller-manager |Execute Status management, manage replication controller |
|kubelet |Run on each node as agent and manage Pod |
|calico |Enable inter-Pod connection using BGP |
|kube-proxy |Configure iptable NAT tables to configure IP and load balance (ClusterIP) |
|etcd |Distribute KVS to store Kubernetes and Calico information |
|etcd-proxy |Run on each node and transfer client request to etcd clusters|
**Tenant Isolation** To enable multi-tenant usage like OpenStack, we utilize OpenStack Keystone for authentication and authorization.
**Authentication** With a Kubernetes plugin, OpenStack Keystone can be used for Authentication. By Adding authURL of Keystone at startup Kubernetes API server, we can use OpenStack OS\_USERNAME and OS\_PASSWORD for Authentication. **Authorization** We currently use the ABAC (Attribute-Based Access Control) mode of Kubernetes Authorization. We worked with a consulting company, Solinea, who helped create a utility to convert OpenStack Keystone user and tenant information to Kubernetes JSON policy file that maps Kubernetes ABAC user and namespace information to OpenStack tenants. We then specify that policy file when launching Kubernetes API Server. This utility also creates namespaces from tenant information. These configurations enable Kubernetes to authenticate with OpenStack Keystone and operate in authorized namespaces. **Volumes and Data Persistence** Kubernetes provides “Persistent Volumes” subsystem which works as persistent storage for Pods. “Persistent Volumes” is capable to support cloud-provider storage, it is possible to utilize OpenStack cinder-volume by using OpenStack as cloud provider. **Networking** Flannel and various networking exists as networking model for Kubernetes, we used Project Calico for this project. Yahoo! JAPAN recommends to build data center with pure L3 networking like redistribute ARP validation or IP CLOS networking, Project Calico matches this direction. When we apply overlay model like Flannel, we cannot access to Pod IP from outside of Kubernetes clusters. But Project Calico makes it possible. We also use Project Calico for Load Balancing we describe later.