---
title: Checking your build configuration
linkTitle: Build checks
params:
sidebar:
badge:
color: green
text: New
weight: 30
description: Learn how to use build checks to validate your build configuration.
keywords: build, buildx, buildkit, checks, validate, configuration, lint
---
{{< summary-bar feature_name="Build checks" >}}
Build checks are a feature introduced in Dockerfile 1.8. It lets you validate
your build configuration and conduct a series of checks prior to executing your
build. Think of it as an advanced form of linting for your Dockerfile and build
options, or a dry-run mode for builds.
You can find the list of checks available, and a description of each, in the
[Build checks reference](/reference/build-checks/).
## How build checks work
Typically, when you run a build, Docker executes the build steps in your
Dockerfile and build options as specified. With build checks, rather than
executing the build steps, Docker checks the Dockerfile and options you provide
and reports any issues it detects.
Build checks are useful for:
- Validating your Dockerfile and build options before running a build.
- Ensuring that your Dockerfile and build options are up-to-date with the
latest best practices.
- Identifying potential issues or anti-patterns in your Dockerfile and build
options.
> [!TIP]
>
> Want a better editing experience for Dockerfiles in VS Code?
> Check out the [Docker VS Code Extension (Beta)](https://marketplace.visualstudio.com/items?itemName=docker.docker) for linting, code navigation, and vulnerability scanning.
## Build with checks
Build checks are supported in:
- Buildx version 0.15.0 and later
- [docker/build-push-action](https://github.com/docker/build-push-action) version 6.6.0 and later
- [docker/bake-action](https://github.com/docker/bake-action) version 5.6.0 and later
Invoking a build runs the checks by default, and displays any violations in the
build output. For example, the following command both builds the image and runs
the checks:
```console
$ docker build .
[+] Building 3.5s (11/11) FINISHED
...
1 warning found (use --debug to expand):
- Lint Rule 'JSONArgsRecommended': JSON arguments recommended for CMD to prevent unintended behavior related to OS signals (line 7)
```
In this example, the build ran successfully, but a
[JSONArgsRecommended](/reference/build-checks/json-args-recommended/) warning
was reported, because `CMD` instructions should use JSON array syntax.
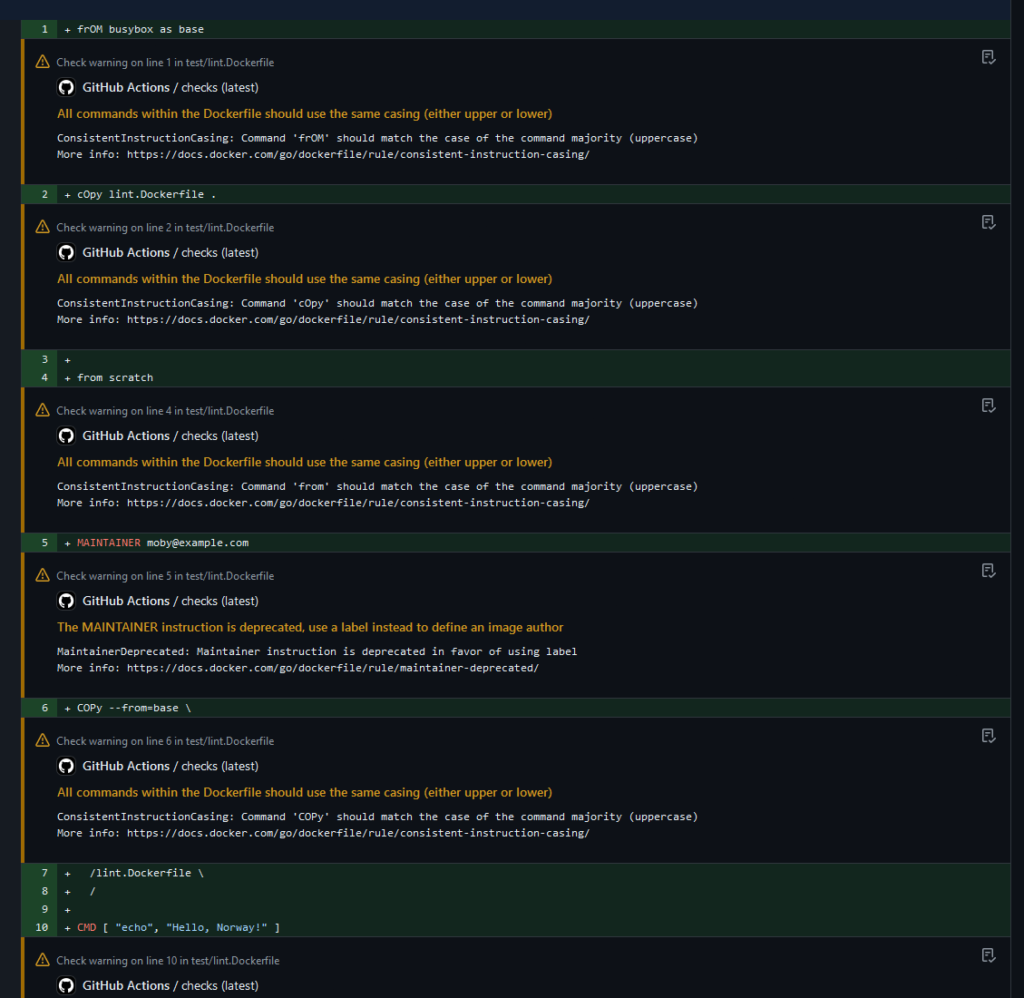
With the GitHub Actions, the checks display in the diff view of pull requests.
```yaml
name: Build and push Docker images
on:
push:
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Build and push
uses: docker/build-push-action@v6.6.0
```