| Allow all images from Docker Hub | `docker.io/*` |
| Allow all Docker Official Images | `docker.io/library/*` |
| Allow images from a specific organization | `docker.io/orgname/*` |
| Allow tags of a specific repository | `docker.io/orgname/repository:*` |
| Allow images on a registry with hostname `registry.example.com` | `registry.example.com/*` |
| Allow slim tags of NodeJS images | `docker.io/library/node:*-slim` |
An asterisk (`*`) matches up until the character that follows, or until the end
of the image reference. Note that the `docker.io` prefix is required in order
to match Docker Hub images. This is the registry hostname of Docker Hub.
This policy is configurable with the following options:
- **Approved base image sources**
Specify the image reference patterns that you want to allow. The policy
evaluates the base image references against these patterns.
Default: `[*]` (any reference is an allowed base image)
- **Only supported tags**
Allow only supported tags when using Docker Official Images.
When this option is enabled, images using unsupported tags of official images
as their base image trigger a policy violation. Supported tags for official
images are listed in the **Supported tags** section of the repository
overview on Docker Hub.
Enabled by default.
- **Only supported OS distributions**
Allow only Docker Official Images of supported Linux distribution versions.
When this option is enabled, images using unsupported Linux distributions
that have reached end of life (such as `ubuntu:18.04`) trigger a policy violation.
Enabling this option may cause the policy to report no data
if the operating system version cannot be determined.
Enabled by default.
Your images need provenance attestations for this policy to successfully
evaluate. For more information, see [No base image data](#no-base-image-data).
### SonarQube Quality Gates
The **SonarQube Quality Gates** policy type builds on the [SonarQube
integration](../integrations/code-quality/sonarqube.md) to assess the quality
of your source code. This policy works by ingesting the SonarQube code analysis
results into Docker Scout.
You define the criteria for this policy using SonarQube's [quality
gates](https://docs.sonarsource.com/sonarqube/latest/user-guide/quality-gates/).
SonarQube evaluates your source code against the quality gates you've defined
in SonarQube. Docker Scout surfaces the SonarQube assessment as a Docker Scout
policy.
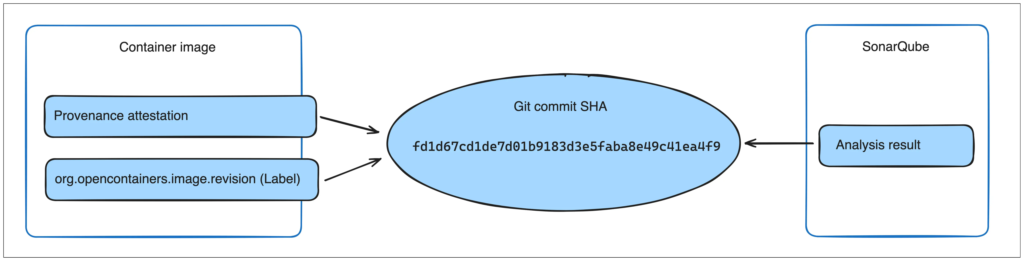
Docker Scout uses [provenance](/manuals/build/metadata/attestations/slsa-provenance.md)
attestations or the `org.opencontainers.image.revision` OCI annotation to link
SonarQube analysis results with container images. In addition to enabling the
SonarQube integration, you must also make sure that your images have either the
attestation or the label.